Updated February 25, 2024: To ensure the optimal experience we will not be implementing the policy as indicated, on February 23, 2024. We will provide an update shortly on the new timing for implementation of the policy. Thank you for your patience.
To enhance protection against Domain impersonation using Microsoft Defender for Office 365, the system will enable Domain impersonation protection by default. Additionally, existing customers who unintentionally kept Domain impersonation protection OFF in their tenant environment will start receiving the benefits of this protection for their company/organization’s owned domains.
[When this will happen:]
Rollout will begin in mid-January 2024, and there will be an option to opt-out. We will provide an update shortly on the new timing for implementation of the policy.
[How this will affect your organization:]
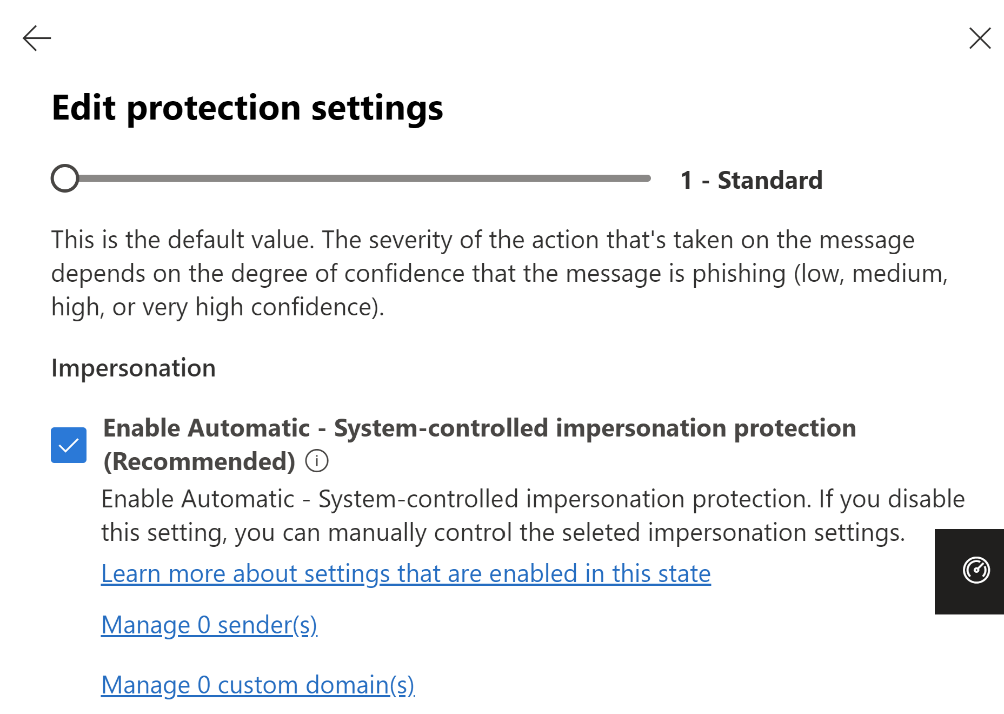
The upcoming change will provide security administrators the capability to manage Domain impersonation protection automatically enabled by default within AntiPhish Default and Custom Policies. This state will only be enabled by default for tenants who have the Domain impersonation setting turned OFF. (Specifically, when AntiPhish policy -> Impersonation settings -> Custom Domains; EnableOrganizationDomainsProtection:False within PowerShell).
Additionally, there will also be an option for admins to choose not to enable these protections by default. They can set ImpersonationProtectionState: Manual in order to opt-out of Automatic state of domain impersonation protection.
When the policy is effective (approx. 30 days after the opt-out period), users will see that domain impersonated emails are handled according to the policy settings chosen by MDO controlled settings as per Automatic state of the protection set by Security admins. (Or by settings configured by the Security admins per Manual state). The configured policies will determine the actions taken for such emails, ensuring that appropriate measures are in place to mitigate the risks associated with Domain impersonation attacks. This provides end users with increased confidence and assurance that impersonated emails will be managed effectively based on the guidelines established by their organization’s security administrators.
Note: This change is only applicable to accepted domains and not applicable to custom domains (i.e. targeted domains) and it does not apply to Preset policies. The following settings will be enabled in Automatic state for Organization Domain Impersonation protection:
- ImpersonationProtectionState – Automatic
- EnableOrganizationDomainsProtection – True
- EnableSimilarDomainsSafetyTips – True
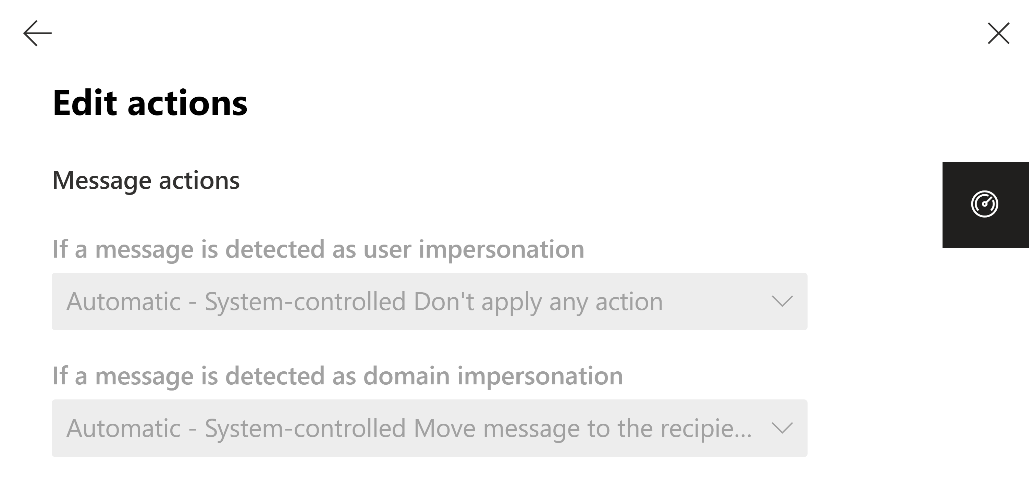
- TargetedDomainProtectionAction – MoveToJmf
[What you need to do to prepare:]
During rollout, only the user experience and cmdlets related to the Domain impersonation protection change will be made available to customers. However, no immediate actions will be taken on domain impersonated messages based on these changes.
Customers have the option to opt out of Automatic state of protection controlled by Microsoft and adjust their settings manually according to their preferences before the effective date. From that date onwards, the chosen setting will be honored, and the Domain impersonation protection will take action accordingly on the messages detected as such. (For example, send to junk or quarantine).
With the upcoming automatic state rollout for Domain impersonation protection, other forms of impersonation protection will be turned OFF, as per the previous policy setting. If you want to activate impersonation protection for all other types of impersonations, you will need to disable the automatic state and manually enable protection settings for each of them.
We are actively planning to introduce automatic state functionality for other impersonation protections in the future such as custom domain and user impersonation protection, mailbox intelligence-based impersonation protection.
For more detailed information about Domain impersonation protection and its configuration in MDO, you can refer to the following public documentation: Anti-phishing policies and Impersonation insight.